Blocking Malicious IP’s using Suricata
In the previous post we saw how we can install Suricata in Ubuntu, in this post let’s see how we can use Suricata to block requests from Malicious IP’s.
You can find Suricata installation guide here.
Before stating we need python and pip installed in the machine,
sudo apt-get update
sudo apt-get install python3
sudo apt-get install python3-pipOnce you have successfully installed python and pip, install requests using pip.
pip install requests
Now head to AbuseIPDB and create an account (free account will work for test purposes, use can go for paid accounts if required) and create an API key and copy the key.

Save the below python code into a file and name it as maliciousIPs.py
import requests
import json
def update_suricata_rules(malicious_ips):
with open('/var/lib/suricata/rules/block_ips.rules', 'a') as rule_file:
sid = 100001
for ip in malicious_ips:
rule_file.write(f'drop ip {ip} any -> any any (msg:"Blocked malicious IP {ip}"; sid: {sid}; rev:1;)\n')
sid += 1
if __name__ == "__main__":
malicious_ips = []
api_key = '<Your API key>'
url = 'https://api.abuseipdb.com/api/v2/blacklist'
headers = {
'Key': api_key,
'Accept': 'application/json'
}
try:
response = requests.get(url, headers=headers)
if response.status_code == 200:
data = response.json()
malicious_ips = [entry['ipAddress'] for entry in data['data']]
print(f"Fetched {len(malicious_ips)} malicious IPs from AbuseIPDB.")
else:
print(f"Failed to fetch IPs. Status code: {response.status_code}")
except Exception as e:
print(f"Error fetching IPs: {str(e)}")
update_suricata_rules(malicious_ips)
Now that the file is saved, run the python file using
sudo python3 maliciousIPs.py
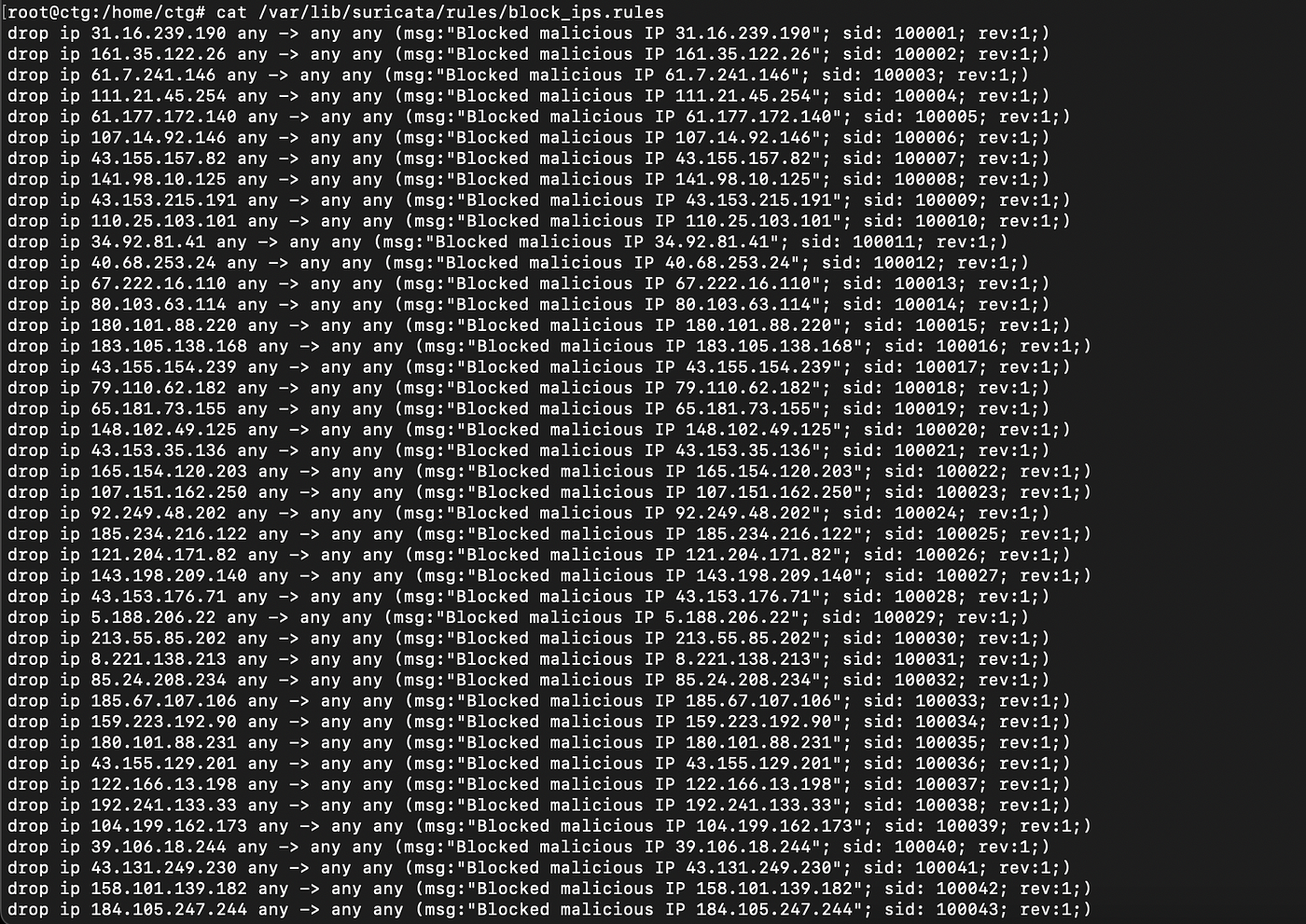
Now let’s check if the python code created a rules file in the directory /var/lib/suricata/rules and check the file.
sudo ls /var/lib/suricata/rules
sudo cat /var/lib/suricata/rules/block_ips.rules
Now let’s edit our suricata.yaml file which is in the directory /etc/suricata/
cd /etc/suricata/
nano suricata.yamlAnd in the end of the file find the part where rule files are defined and add the new rules file that we just created.
default-rule-path: /var/lib/suricata/rules
rule-files:
- suricata.rules
- block_ips.rules
Save and exit the yaml file. Now update the suricata using,
sudo suricata-update
If you have come this far, you can now successfully malicious IP’s. Let’s test the work using,
sudo tail -f /var/log/suricata/fast.log
We can see that IP address 152.32.206.38 is been blocked multiple times, let’s check the details about this IP address using whoismyisp.

This IP address looks to be from Virgina, lets check more details using Virustotal.

From Virustotal we can see that multiple vendors have flagged this IP address to be malicious in various ways (like phishing, suspicious etc).
We can go ahead and also look up for the graph preview.

So that’s all for this post, if you found this post informative give a applaud and drop a comment and share your views and suggestions. Please consider giving a follow that would really motivate me to write more such posts.
Also check out and subscribe to the YouTube channel: https://www.youtube.com/@CyberToolGuardian/featured
Follow us on Instagram:
https://instagram.com/cybertoolguardian
Check out the website:
https://cybertoolguardain.com
Comments
Post a Comment